
The shared responsibility model
First, what’s the shared responsibility model? Well, to design a well-architected application, AWS suggests following six pillars. Among these six pillars, one is security. Security includes sharing responsibility between AWS and the customer. In particular, and I quote,
Customers are responsible for managing their data (including encryption options), classifying their assets, and using IAM tools to apply the appropriate permissions.
Beautiful, isn’t it? AWS gives us a powerful tool, IAM, to manage permissions; we have to configure things in the best way, and AWS gives us the way to do so. Or does it? Let’s take a look together.
Our goal
Our goal is quite straightforward: setting up a Kubernetes cluster for our developers. Given that AWS offers AWS EKS, a managed Kubernetes service, we only need to configure it properly, and we are done. Of course, we will follow best practices to do so.
A proper setup
Of course, we don’t use the AWS console to manually configure stuff, but Infrastructure as Code: basically, we will write some code that will call the AWS APIs on our behalf to set up AWS EKS and everything correlated. In this way, we can have a reproducible setup that we could deploy in multiple environments, and countless other advantages.
Moreover, we want to avoid launching scripts that interact with our infrastructure from our PC: we prefer not to have permissions to destroy important stuff! Separation of concerns is a fundamental, and we wish to write code without worrying about having consequences on the real world. All our code should be vetted from somebody else through a merge request, and after being approved and merged to our main branch, a runner will pick it up and apply the changes.
We are at the core of the problem: our runner should follow the principle of least privilege: it should be able to do only what it needs to do, and nothing more. This is why we will create a IAM role only for it, with only the permissions to manage our EKS cluster and everything in it, but nothing more.
I would have a massive rant about how bad is the AWS documentation for IAM in general, not only for EKS, but I will leave it to some other day.
The first part of creating a role with minimum privileges is, well, understanding what minimum means in our case. A starting point is the AWS documentation: unfortunately, it is always a bad starting point concerning IAM permissions because it is always too generous in allowing permissions.
The “minimum” permission accordingly to AWS
Okay, hardening this will be fun, but hey, do not let bad documentation get in the way of a proper security posture.
You know what will get in the way? Bugs! A ton of bugs, with absolutely useless error messages.
I started limiting access to only the namespace of the EKS cluster I wanted to create. I ingenuously thought that we could simply limit access to the resources belonging to the cluster. But, oh boy, I was mistaken!
Looking at the documentation for IAM resources and actions, I created this policy:
1{ 2 "Version": "2012-10-17", 3 "Statement": [ 4 { 5 "Effect": "Allow", 6 "Action": [ 7 "eks:ListClusters", 8 "eks:DescribeAddonVersions", 9 "eks:CreateCluster"10 ],11 "Resource": "*"12 },13 {14 "Effect": "Allow",15 "Action": "eks:*",16 "Resource": [17 "arn:aws:eks:eu-central-1:123412341234:addon/my-cluster/*/*",18 "arn:aws:eks:eu-central-1:123412341234:fargateprofile/my-cluster/*/*",19 "arn:aws:eks:eu-central-1:123412341234:identityproviderconfig/my-cluster/*/*/*",20 "arn:aws:eks:eu-central-1:123412341234:nodegroup/my-cluster/*/*",21 "arn:aws:eks:eu-central-1:123412341234:cluster/my-cluster"22 ]23 }24 ]25}Unfortunately, if a role with these permissions try to create a cluster, this error message appears:
1Error: error creating EKS Add-On (my-cluster:kube-proxy): AccessDeniedException: User: arn:aws:sts::123412341234:assumed-role/<role>/<iam-user> is not authorized to perform: eks:TagResource on resource: arn:aws:eks:eu-central-1:123412341234:/createaddonI have to say that at least the error message gives you a hint: the /createddon action is not scoped to the cluster.
After fighting with different polices for a while, I asked DuckDuckGo for a help, and indeed somebody reported this problem to AWS before, in this GitHub issue.
What the issue basically says is that if we want to give an IAM role permission to manage an add-on inside a cluster, we must give it permissions over all the EKS add-ons in our AWS account.
This of course breaks the AWS shared responsibility principle, ‘cause they don’t give us the tools to upheld our part of the deal. This is why it is a real and urgent issue, as they also mention in the ticket:
Can’t share a timeline in this forum, but it’s a high priority item.
And indeed it is so high priority, that it has been reported the 3rd December 2020, and today, more than one year later, the issue is still there.
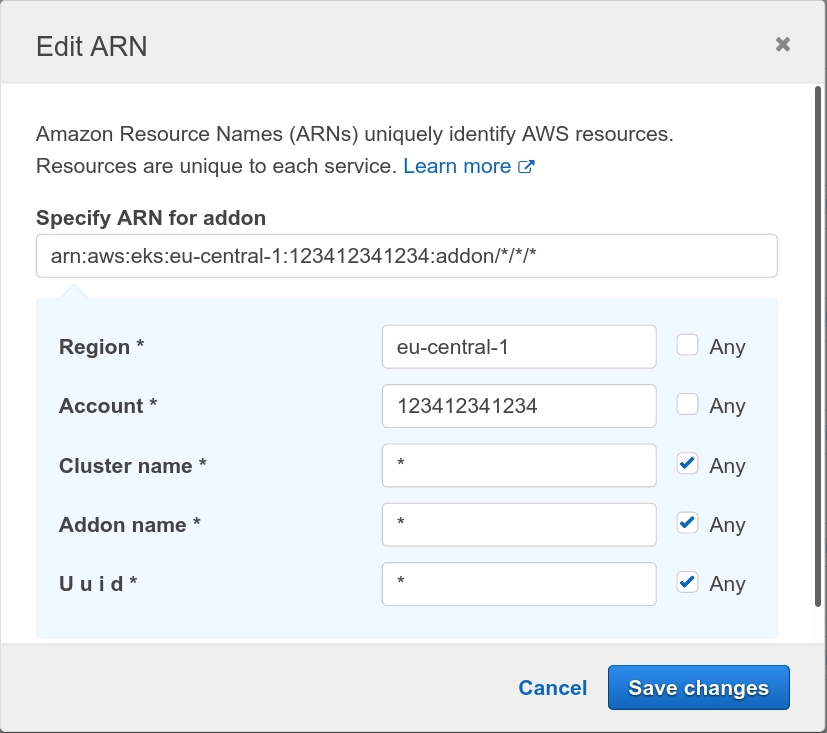
To add insult to the injury, you have to write the right policy manually because if you use the IAM interface to select “Any resource” for the add-ons as in the screenshot below, it will generate the wrong policy! If you check carefully, the generated resource name is arn:aws:eks:eu-central-1:123412341234:addon/*/*/*, which of course doesn’t match the ARN expected by AWS EKS. Basically, also if you are far too permissive, and you use the tools that AWS provides you, you still will have some broken policy.
Do you have some horror story about IAM yourself? I have a lot of them, and I am thinking about a more general post. What do you think? Share your thoughts in the comments below, or drop me an email at [email protected].
Ciao,
R.

Comments